How to Start Your Security Governance Journey (Part 1)
Security Governance Through Principles and Policies
Security must start somewhere, and that beginning is with principles and policies. Understanding the foundational pillars of security helps organisations build strong, resilient systems that align with both business and regulatory objectives.
Understanding and Applying Confidentiality, Integrity and Availability (CIA Triad)
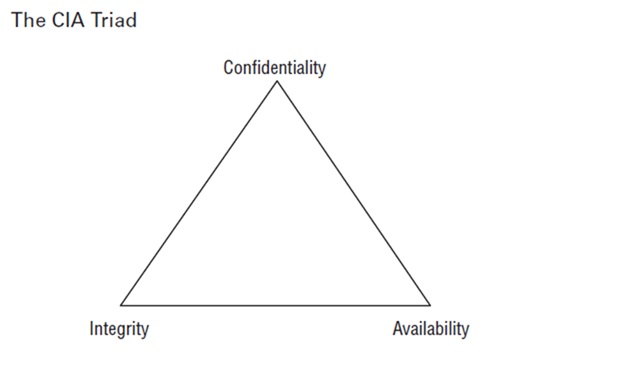
The CIA Triad—Confidentiality, Integrity, and Availability—is one of the first and most fundamental concepts in information security. It serves as the foundation upon which all security mechanisms and governance frameworks are built.
Confidentiality
Confidentiality means protection against unauthorised access. When a security mechanism offers confidentiality, it provides a high level of assurance that the system is resilient against unauthorised data access.
Confidentiality is maintained through:
- Proper access controls that govern the relationship between subjects (users) and objects (data)
- Encryption, network padding, authentication mechanisms, administrative controls, and physical security
- Data classification and personnel training, which strengthens confidentiality across the organisation
Confidentiality and integrity are interdependent—without integrity (the assurance that data cannot be modified without permission), confidentiality cannot be maintained.
Other concepts related to confidentiality:
- Sensitivity: The degree to which the information could cause harm or damage if disclosed (e.g., patient data is sensitive)
- Discretion: The ability of a subject to influence disclosure
- Criticality: The importance of the information. Mission-critical data must be protected with the highest level of confidentiality
- Concealment: The act of hiding information to protect confidentiality (e.g., concealing a webhook URL)
- Secrecy: The ability to prevent the disclosure of personal or confidential information
- Privacy: Preventing unauthorised access to personally identifiable information (PII)
- Seclusion: Storing something in a controlled, out-of-the-way location with tight access controls
- Isolation: Keeping processes or data separated from one another for security reasons
Integrity
Integrity ensures the completeness, accuracy, and reliability of data. While confidentiality protects against unauthorised access, integrity protects against unauthorised alteration.
For integrity to be maintained:
- Unauthorised subjects must not be able to alter objects
- Authorised subjects must not make unauthorised modifications
- Data must maintain internal and external consistency and accurately reflect real-world information
- Mechanisms such as hash verification provide protection against integrity violations.
Other concepts pertaining to integrity:
- Accuracy: Being correct and precise
- Truthfulness: Being the true reflection of reality
- Authenticity: Being authentic and genuine
- Validity: Being factually sound
- Non-repudiation: Subject cannot deny having performed the action
- Responsibility: Being in charge of the data
- Comprehensiveness: Being complete in scope
Availability
Availability ensures that data and systems are accessible when needed. A properly available system is protected against both software-based attacks (e.g., DoS attacks) and environmental threats (e.g., power failures, floods).
Availability goes hand in hand with confidentiality and integrity.
Key Concepts of Availability
- Usability: The system should be easy to understand and operate
- Accessibility: Resources must be available to authorised users regardless of capability or limitation
- Timeliness: Access must occur within a reasonable and expected time frame
Other Core Security Concepts: The AAA Model
The AAA model—Authentication, Authorisation, and Auditing—is another foundational concept in secure systems.
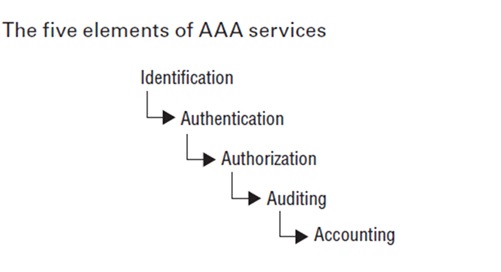
- Identification: The process of identifying a user. Every user must present an identity (e.g., username) before system access
- Authentication: Verifying the claimed identity using one or more factors (e.g., PIN, password, or device)
- Authorisation: Granting access to resources based on permissions (e.g., role-based or rule-based access control, MAC, or DAC)
- Auditing: Recording user actions for future review (e.g., system event logs)
- Accountability: Ensuring non-repudiation—users cannot deny their actions, and system activity can be traced meaningfully
Protection Mechanisms
CIA principles are implemented through security controls, each of which may consist of one or more protection mechanisms:
- Layering (Defence-in-Depth): Implementing multiple layers of security—physical, administrative, technical, and logical
- Abstraction: Grouping similar security elements to simplify permission assignment (e.g., role-based access control)
- Data Hiding: Concealing data from unauthorised users (e.g., restricting database views)
- Encryption: Ensuring data confidentiality and integrity when stored (at rest), transmitted (in transit), or processed (in use)
Evaluating and Applying Security Governance Principles
Security governance combines elements of corporate and IT governance. While corporate governance ensures business growth and sustainability, IT governance ensures that growth remains secure and supported by technology.
Key considerations:
- Security governance is influenced by local laws and regulatory requirements
- Security is no longer just an IT issue—it is a business responsibility
- Governance should ideally be led by a board-level security committee or equivalent oversight body
- Notable governance standards include NIST 800-53 and NIST 800-100
- Aligning the Security Function with Business Strategy, Goals, and Objectives
Security management planning must align with the organisation’s mission and objectives. Every security initiative should be supported by a business case that defines benefits, costs, and risks.
The top-down approach is most effective:
- Senior management defines high-level policies
- Middle management translates them into operational and technical controls
- Employees execute and comply with the implemented processes
- The Chief Information Security Officer (CISO) should report directly to senior leadership, ensuring autonomy and avoiding internal politics
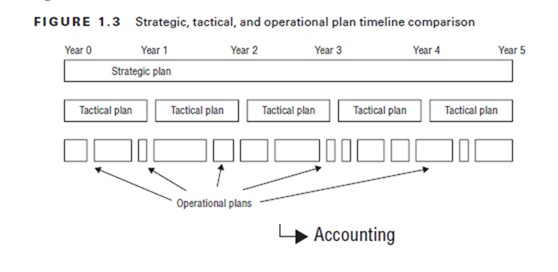
Security Planning Levels
Security planning operates at three distinct levels:
- Strategic Plan: A long-term (typically 5-year) plan outlining high-level goals and future direction
- Tactical Plan: A mid-level, annual plan that includes cost, licensing, and project considerations
- Operational Plan: A detailed, short-term plan defining daily or project-specific activities
Security, like IT, is an ongoing process—goals evolve as technology and threats change.
Further reading can be found at ISC2 / CISSP.